Seeking to prevent the smuggling of people, goods and drugs, international border agencies are faced with criminals and gangs who are increasingly using sophisticated technology to plan, coordinate, and perpetrate their activities.
Responding to these challenges, a new era of advanced crime analytics is helping to detect and disrupt such activities. Emerging techniques rely on innovative data analytic tools, such as social network analysis, to identify subtle relationships, and uncover hidden patterns and anomalies.
Border control agents require the eyes of a hawk, a good understanding of human psychology and endless patience. But even with these attributes, border control is still a gamble. How do you know you’ve stopped the right person? For every incorrect stop and search, the real person of interest may slip quietly past and into the country carrying contraband goods, illegal drugs or even be trafficked there themselves and heading for a dangerous future. Then there’s the organised traffickers and gangs.
It’s a recipe that no doubt adds to an already stressful job for law enforcement agencies charged with securing a nation’s ports of entry: on the one hand, large and increasing volumes of cargo and traffic and, on the other, increasingly sophisticated and well-organised smugglers and cross-border criminal organisations that know how to use – and often evade – technology to ply their illegal activities.
This certainly does not deter officials. In the U.S. alone, on a typical day more than 60,000 Customs and Border employees screen some 67,000 cargo containers, arrest more than 1,100 individuals and seize nearly six tons of illicit drugs1.
The scenario is similar in the United Kingdom. The UK Border Force’s 8,000 strong staff must operate customs controls at 138 air, sea and rail ports across the UK to prevent illegal goods entering the country and to detect human traffickers and their victims2. But with criminal patterns and techniques evolving constantly, border agencies must continue to adapt to changing and emerging threats.
Indeed, the current European migrant crisis demonstrates the increasing involvement of criminal gangs in people trafficking, and whose profits rival those of narcotics and arms trafficking. European officials are only just beginning to piece together a complete picture of international organised crime networks who are profiting from refugees desperate to flee war and persecution.
Commenting on the current crisis, Yury Fedotov, the Executive Director of the UN Office on Drugs and Crime, said "We cannot allow desperate people, escaping conflict and humanitarian disasters, to fall prey to organised crime. We need urgent and resolute action to save lives and punish the criminals."3.

Cyber Evidence
The Victorians attempted to identify criminals using common physical traits, giving rise to the notion that you could tell someone was ‘evil’ simply by looking at their face, believing that a low brow meant they were less evolved4. This ultimately unscientific and unsuccessful analysis nevertheless highlighted an interest in techniques which could prevent crime before it even happened.
In the 19th century, the use of fingerprints revolutionised the criminal justice process. More recently, modern advances in the ability to search DNA records of known offenders, or link seemingly discrete criminal incidents via DNA traces found at crime scenes, has made a significant contribution to increasing detection rates5.
Today, we are on the cusp of a technological evolution in the use of computer-driven analytics, which could prove as revolutionary for catching online traffickers and gangs as fingerprints and DNA were to the law enforcement community in catching the perpetrators of physical crimes.
Border criminals become more tech-savvy
Criminal justice practitioners are now facing a rapidly changing landscape where the facilitation of crime is dominated by technology. It plays an influential and growing role in connecting and aiding criminal networks that engage in trafficking of humans, narcotics, weapons, money and other contraband. By utilising multiple communications devices and applications, offenders are able to plan, coordinate, and perpetrate their activities with increased mobility, while concealing their digital footprint.
For example, smugglers have begun to use cyber-attacks to facilitate border crime. In the Belgian port of Antwerp, an organised criminal network successfully transported large shipments of heroin and cocaine concealed as legitimate goods from South America for a period of over two years. The drug traffickers recruited hackers to infiltrate IT systems controlling the movement and location of containers. Armed with this data, the traffickers were able to intercept and steal these containers before the harbour staff encountered them6.
Commenting on the case, which was solved in late 2013, Europol Director Rob Wainwright said, “[It] is an example of how organised crime is becoming more enterprising, especially online,” adding, “What it means therefore is that the police need to change the way they operate - they have to become much more tech savvy,"7.
Crime analytics connects the dots
An approach that has gained significant traction in recent years is computer-driven data analytics. Once confined to the realm of policy advisors, researchers and academics, the rapid growth of computer processing power coupled with its increased affordability has empowered front-line police and investigators with data analytic tools, which can quickly process and analyse large volumes of data from numerous sources to perform quantitative statistical analysis, identify relationships, uncover hidden patterns and anomalies8.
Advanced crime analytics tools can rapidly process and analyse large volumes of data held on devices such as mobile phones, laptops and PCs, which are often seized at the border, allowing investigators to detect suspicious activities and uncover unusual relationships. The ability to process and interrogate such data quickly and efficiently, often while a suspect is being held, can be critical to the success of an investigation.
Social network analysis
A key aspect of uncovering these hidden patterns and relationships lies in social network analysis. Here we are not talking about analysis of simply online social networks such as Twitter or Facebook, but rather complex networks of people, organisations and other entities who may be directly or indirectly linked to one other. It is a data mining technique that visualises large volumes of data as a set of interconnected entities. The concept is not too dissimilar to the classic evidence pin board, from any detective TV series or movie, showing photos of criminal actors and their links to one another.
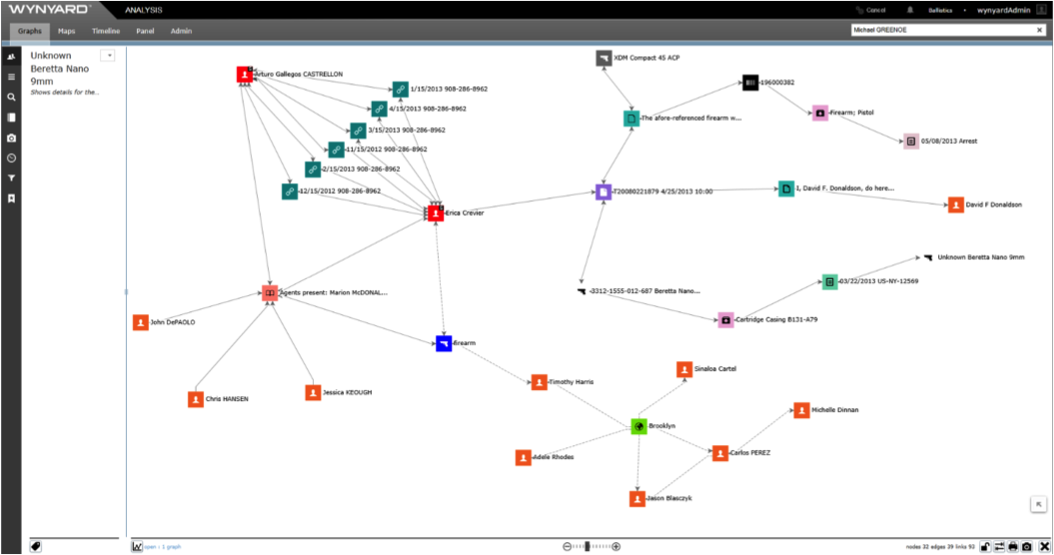
Individual criminal actors are represented as nodes, along with locations, gangs, bank accounts, etc. These nodes are then linked together representing relationships between the entities; such as communication, offender movement, known associates. As the network expands, patterns and hidden relationships can be uncovered by statistical methods.
A primary use of social network analysis is to identify key actors by asking the question “Which are the most influential nodes within my system?” Here, influence is determined by factors such as the number of relationships a node has, how influential the connected nodes are and how often a node forms the shortest path between other nodes. With these analytical techniques, highly influential actors holding key central positions can be identified, guiding law enforcement on who to focus effort and resource towards to disrupt criminal networks.
Analytics in action
In 2012, customs officers at the border of a busy southern hemisphere country intercepted a person of interest who was suspected of being a child sex offender.
During the interception, officers seized a USB memory stick which was interrogated using crime analytics tools in a forensically safe process. A number of images on the device were quickly identified as being offensive in nature. Further analysis of data from the image files allowed metadata, including geotags, to be extracted and used to determine the origin of the images. Within 24 hours of the interception, the location data and other evidence had been provided to authorities in another country and were used to raid the suspect’s premises, where a number of abused children were rescued9.
This case highlights issues that have previously frustrated law enforcement agencies who are faced with investigating data held on digital devices obtained from suspects. The tools required to perform this kind of digital forensic analysis are often inconveniently located meaning seized digital devices must be transported before they can be processed. A large backlog of digital devices, coupled with only a few digital forensic experts available to perform the data extraction, means the data cannot be examined in a timely fashion. In this case, the suspect may have escaped detection10.
In addition to identifying anomalous and suspicious patterns of behaviour, advanced crime analytics tools can integrate data from many disparate sources, including criminal watch lists, bank and financial transactions, travel and transaction records, and cargo and manifest records to build an even more comprehensive picture. Investigators are able to reveal connections and relationships that would have otherwise gone unnoticed, allowing them to find, monitor, track, assess and disrupt trafficking networks.
For example, in some countries victims of human trafficking are most likely to know the offender, who is often a family member, friend or trusted individual. Where data sharing agreements exist, data analytics software has the ability to link information from multiple government or non-profit agencies aimed at protecting and identifying vulnerable people who are the potential targets of traffickers. When agencies have the ability to analyse the large datasets available to them, and use patterns of relationships between families, associates and known offenders to create a holistic picture, then can then adopt a proactive approach to protecting potential victims.
Border protection agencies operate in complex and ever-changing environments, where international criminal networks and smugglers continue to innovate and become more tech-savvy. As new dangers arise, having the ability to adapt and respond quickly is vital to the protection of ports, people and property. The application of advanced crime analytics is one way law enforcement agencies are detecting and disrupting border crime. With this tool, agencies can dramatically increase their ability to identify individuals and organisations of interest, share critical information, and strengthen the fight against border crime.








